When operating in the cloud, whether you’re already deploying your workloads or planning to, and choosing Azure for its robust feature set, security will be at the forefront of your concerns. Whether managing virtual machines, container instances, or web applications, ensuring security is crucial alongside reliability, maintainability, and cost optimization.
What Azure Network Security Solutions Currently Exist?
- Azure Network Security Groups (NSGs)
- Azure Firewall
- Azure Web Application Firewall (WAF)
- Azure FrontDoor
- Azure DDoS Protection
What Solution is Right for Me?
Before choosing the solution it’s important to know what they are and how you could benefit from them. So let’s introduce all of them
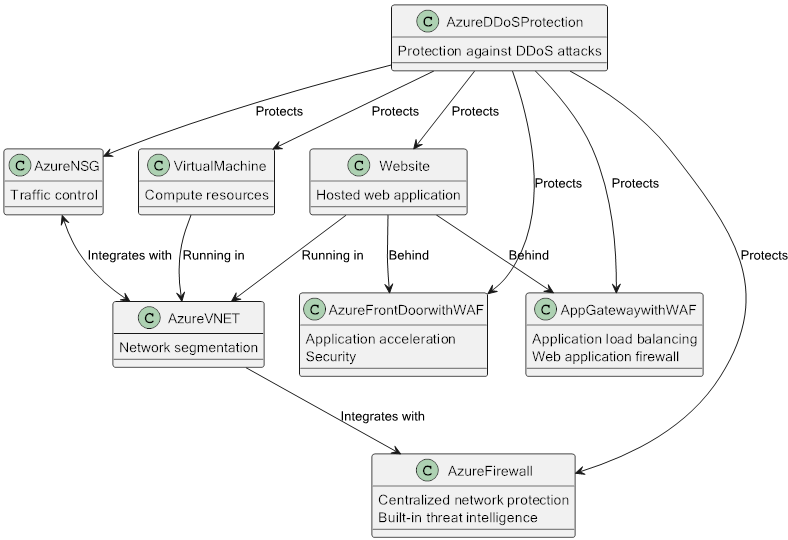
Starting off with the first thing that comes to mind will likely be the network security group or NSG. This free feature is automatically added as soon as you deploy a Virtual Network or VNET. You can have multiple attached to a single virtual network for different purposes. The down part is that it only protects at a layer 4 level so like traffic control.
Second would be the firewall which operates at layers 3, 4, and 7. It allows for traffic inspection and centralizing outbound traffic to ensure the Azure resources cannot go “anywhere” on the internet, but can only reach resources that are required. Since it operates on all those layers it can handle traffic on both TCP, HTTP, HTTPS, and UDP across a range of ports, which allows for more flexibility when protecting your workloads
The third contestant is the Azure Application Gateway (WAF). The Azure Application Gateway is a gateway that allows traffic either internally or externally to reach your application by defining listeners. The application gateway can handle traffic on HTTP (port 80) and HTTPS (port 443). The application gateway also comes with a (paid) option to have an integrated (web application) firewall that protects on layer 7 to ensure inbound traffic is not only load balanced (as is a feature of the application gateway), but traffic is also inspected and blocked based on conditions like geographic origin or rate limiting.
The fourth is an odd one for sure… Azure Front Door. It is the only global resource of the bunch, which allows for a lot of flexibility. It is typically used when you either have APIs, websites or want to make files accessible globally. It offers global load balancing along with a web application firewall and DDOS protection at layers 3 and 4.
Finally, we have the Azure DDOS protection, Which is a plan that protects your Azure Resources. It works with either VNET, Traffic Manager, or an application gateway (WAF), and allows for taking action upon discovering threats. There are 2 differentiating options, to secure on a network level (specific to a VNET) or IP level (protects on a per-ip basis, with DDOS Rapid Response Support with a discount on WAF)
Here’s a quick comparison starting with a quick overview
| Feature/Aspect | Azure NSGs | Azure Firewall | Azure Application Gateway (WAF) | Azure Front Door | Azure DDoS Protection |
|---|---|---|---|---|---|
| Primary Purpose | Network segmentation and traffic control | Centralized network protection | Web application protection | Application acceleration and security | Protection against DDoS attacks |
| Layer of OSI Model | Layer 4 | Layer 3, 4, 7 | Layer 7 | Layer 3, 4, 7 | Layer 3, 4, 7 |
| Stateful Inspection | No | Yes | No | Yes | N/A |
| Threat Intelligence | No | Yes (built-in intelligence) | No | No | Yes |
| Default Logging and Analytics | Basic | Advanced | Basic | Advanced | Integrated with Azure Monitor |
| Integration | Integrates with VNets | Integrates with with VNets, integrates with Azure Security Center | Part of Application Gateway | Integrates with Azure VNET, Azure WAF and Traffic Manager for optimized security and traffic distribution | Integrates with VNET and protects with any VNET-deployable resource in layer 3,4 and 7 like Azure Firewall and WAF(frontdoor/application gateway) |
| Typical Use Cases | Segregating network traffic | Centralized traffic filtering | Web protection | Global load balancing, Global WAF (e.g. in front of a set of applications/APIs) and DDOS protection (layers 3 and 4) | Mitigating DDoS attacks |
| Deployment Scope | VNets and subnets | VNets and hybrid environments | Application layer | Global | Network layer |
Conclusion
No single solution fits all scenarios perfectly, and you’ll often find these technologies working together to offer robust protection. A Web Application Firewall is best suited for targeting specific applications, while Network Security Groups are effective on individual VMs or resources. For overarching security, services like Azure Firewall, Front Door, and DDoS Protection cater to broader and more complex environments. Use the table above to guide your decisions based on specific needs.
Leave a Reply